Comprehensive Guide to Webroot Anti-Spyware Features


Intro
In a world where our lives are increasingly intertwined with digital landscapes, understanding the importance of online security has never been more crucial. With every click, swipe, and tap, we risk exposing ourselves to a myriad of potential threats. These include malicious programs, phishing scams, and insidious spyware that can infiltrate our systems, steal sensitive information, and compromise our privacy.
In this comprehensive guide, we'll dive deep into Webroot Anti-Spyware, interpreting its role as a frontline defense against these digital evildoers. From exploring its standout features to discussing best practices for enhancing online safety, this exploration caters to everyone—from the savvy tech enthusiast to those just beginning their journey into the realm of cyber security.
Let's unpack the details.
Overview of Cyber Security Threats
Cyber threats loom large in today's internet-connected world. Here we breakdown the various types and their impact on everyday users.
Types of cyber threats
Cyber threats come in various shapes and sizes. Among the most prevalent are:
- Malware: Short for malicious software, this includes viruses, worms, and trojans designed to damage or disrupt systems.
- Phishing: Deceptive attempts to gather sensitive information, often made appearing legitimate through emails or websites that mimic trusted entities.
- Ransomware: A type of malware that locks users out of their system or files until a ransom is paid.
Statistics on cyber attacks
Recent studies reveal alarming trends:
- It's projected that a new cyber-attack occurs every 39 seconds.
- Over 50% of small businesses reported a cyber attack in the past year.
Real-life examples of security breaches
- Equifax Breach (2017): Personal data of 147 million Americans were stolen due to unpatched software vulnerabilities.
- Yahoo Breach (2013-2014): More than 3 billion accounts were compromised, marking one of the largest data breaches in history.
"Cyber security is not a product, but a process."
— Bruce Schneier
Best Practices for Online Security
In the face of these threats, fortifying your defenses is paramount. Here are effective strategies to bolster your online safety:
- Strong password creation and management techniques: Use complex combinations of letters, numbers, and symbols. Consider employing a password manager to keep track of multiple logins.
- Regular software updates and patches: Keeping your system and applications updated closes security gaps that cybercriminals exploit.
- Two-factor authentication implementation: Adding an extra layer of security makes it significantly harder for attackers to gain unauthorized access.
Reviews of Security Tools
With countless antivirus and security software available, selecting the right tool can be daunting. Evaluating effectiveness is key:
- Antivirus software effectiveness: Test scores from independent labs can offer insight into how well software like Webroot detects and neutralizes spyware.
- Comparison of firewall protection: A robust firewall can serve as a first line of defense. Compare their features based on user reviews and tests.
- Assessment of password managers: Look for features such as encryption, usability, and ease of recovery.
Tips for Ensuring Online Privacy
It's not just about keeping threats at bay; it's also about maintaining your privacy online. Here are some steps to secure your personal information:
- Importance of using VPNs for secure browsing: A VPN masks your IP address, providing anonymity and security, especially on public Wi-Fi networks.
- Privacy settings on social media platforms: Regularly revise your privacy settings to control who can see your posts and personal information.
- Protecting personal data when making online transactions: Ensure you shop on secure websites; look for URLs starting with "https://" which indicate a secure connection.
Educational Resources and Guides
To enhance your understanding and effectiveness in online security, consider the following resources:
- How-to articles on setting up encryption tools: These can provide step-by-step instructions to encrypt files and communications.
- Step-by-step guides on spotting phishing emails: Identifying the hallmarks of phishing can save your personal data from falling into the wrong hands.
- Cheat sheets for quickly enhancing online security practices: Quick references can help you remember key security practices without needing extensive manuals.
By addressing these crucial aspects with clarity and depth, we hope to foster a more secure online experience. This guide aims to navigate the complexities of digital safety and provide insights that can lead to informed decisions regarding tools like Webroot Anti-Spyware.
Understanding Anti-Spyware
In today’s digital landscape, where threats are lurking just a click away, understanding anti-spyware becomes paramount. This section aims to shed light on what anti-spyware is, how spyware operates, and why having strong anti-spyware solutions is essential for anyone concerned about their online security and privacy.
What is Anti-Spyware?
Anti-spyware refers to software designed specifically to detect and eliminate spyware programs from computer systems. Spyware, in essence, is malicious software that operates secretly, often capturing personal information without the user’s knowledge. Anti-spyware tools function as a safeguard against such threats, fighting back in the ongoing battle for your data.
While most users might have heard of antivirus software, anti-spyware is a more focused solution. It targets spyware specifically, ensuring that programs designed to track your online activity, collect sensitive information, or disrupt your computer's operations are kept at bay. You can think of anti-spyware as the security guard who does a thorough check on who is trying to enter your digital premises. 🔒
How Spyware Works
Spyware can sneak into your system in a variety of ways. Often, it is bundled with free software downloads. Users, motivated by the allure of free tools or applications, might inadvertently accept permission for spyware to install itself. This leads to a scenario where the user unwittingly invites a guest who has no intention of leaving.


Once inside, spyware operates covertly—tracking browsing habits, collecting keystrokes, or even hijacking personal data such as passwords or credit card information. This behavior distinguishes spyware from other forms of malware because, unlike a virus that outright disrupts, spyware camouflages itself, often utilizing legitimate processes to avoid detection. Unfortunately, by the time users recognize it, the damage is often already done.
Importance of Anti-Spyware Solutions
The rising reliance on the internet for daily tasks—from online shopping to banking—profoundly increases the need for robust anti-spyware solutions. Essential benefits include:
- Personal Privacy: The primary advantage is safeguarding personal information. No one wants prying eyes following their every move online or stealing sensitive data like social security numbers.
- System Performance: Spyware can bog down your computer, leading to a frustrating experience while browsing or performing essential tasks. Anti-spyware ensures your system runs optimally.
- Peace of Mind: In an age of increasing cyber threats, knowing that anti-spyware is active works wonders for one’s mental peace.
- Legal Protections: In many regions, data breaches can have legal ramifications for companies. Thus, having strong protective measures in place is not just wise—it's often necessary.
"Investing in anti-spyware is not just about preventing attacks; it's about maintaining control over your digital identity."
Ultimately, anti-spyware is not just an option; it's a crucial tool in the arsenal of anyone that values their privacy and security in the digital realm. Keeping yourself informed about the ins and outs of anti-spyware enhances your ability to navigate online safely.
An Preface to Webroot
Understanding the Foundation of Your Online Security
When tackling the ever-evolving landscape of online threats, having a solid answer to the question of security is pivotal. Webroot emerged as a key player in this arena, offering solutions that are both robust and user-friendly. Many people today find themselves caught in the crossfire of spyware and other malicious elements, which makes understanding Webroot essential. Not only does it provide a shield against threats, but it also ensures that your personal information remains safeguarded.
Overview of Webroot Technologies
Webroot Technologies has made a name for itself by harnessing cloud technology to deliver a suite of security solutions. This cloud-based approach offers several benefits:
- Speedy Scanning: Traditional anti-virus systems often bog down your system with hefty updates and scans. With Webroot, the cloud-hosted database means scans are swift without hogging your resources.
- Up-to-Date Protection: Because threat information is processed in the cloud, Webroot users receive real-time updates. This feature ensures that users are protected from the latest security threats almost as soon as they emerge.
- User-Friendly Experience: The interface is designed with simplicity in mind, allowing easy navigation for both tech-savvy users and those new to online security.
In a world where malware can mutiply overnight, understanding how these technologies work together is key to ensuring that you’re not left vulnerable.
History and Development of Webroot Anti-Spyware
Delving into the history of Webroot gives insight into how it has grown into a trusted name in cybersecurity. Founded in 1997, the company has continually adapted to the changing landscape of online risks. Here are some highlights:
- Establishment and Early Days: Webroot initially started with a focus on consumer anti-spyware solutions, an area that was becoming increasingly vital in the late '90s and early 2000s.
- Innovative Shifts: The launch of their cloud-based system in the late 2000s marked a monumental shift in how anti-spyware products were delivered. Instead of bulky software installs that slowed down devices, users could get the same level of protection with far less impact.
- Ongoing Development: Webroot has consistently improved its tools, adding features that respond to new threats like ransomware and advanced persistent threats. Their ongoing development is driven by user feedback as well as emerging security trends.
As cybersecurity continues to burgeon into a complex field, Webroot remains a pivotal figure, reflecting both innovation and reliability for users who prioritize their online safety.
"In an age where threats loom large, understanding your defense mechanisms is no longer optional; it’s imperative."
Key Features of Webroot Anti-Spyware
Understanding the key features of Webroot Anti-Spyware is vital for anyone looking to enhance their online safety. This program stands out for its proactive defense mechanisms, adaptable to the ever-evolving landscape of digital threats. Below, we delve into four fundamental features that significantly contribute to Webroot's effectiveness in safeguarding your system against spyware and other malicious entities.
Real-Time Protection
The hallmark of Webroot Anti-Spyware is its real-time protection feature. This protective layer operates continuously, scanning files and applications as they're being accessed—effectively acting like a vigilant sentry standing guard. Not only does this feature recognize known spyware, but it also identifies suspicious behaviors typical of new threats. The advantage is clear: having real-time protection means you don’t have to wait for a traditional scan to know your system is secure. Users can rest easier knowing their online activities are monitored closely.
Automatic Updates
Another crucial aspect is the automatic updates feature. Webroot constantly updates its virus definition database, ensuring its protection against the latest spyware threats. Because the threat landscape is always in flux, this function helps maintain the software’s effectiveness without requiring manual intervention from users. It’s akin to having a personal bodyguard who is always in the loop, adapting to new threats. Users can enjoy peace of mind without the hassle of frequent manual updates, allowing for seamless operations.
Behavioral Detection
Webroot goes a step further with its behavioral detection capabilities. Instead of relying solely on predetermined signatures of known spyware, this feature analyzes the behavior of software in real time. If an application starts to act maliciously—like trying to access sensitive data or spreading to other files—the software can intervene promptly. This proactive approach can catch sneaky spyware that doesn’t yet have a definitive signature in the database. Thus, users benefit from an adaptive defense system that listens closely for suspicious activity.
Cloud-Based Scanning
The cloud-based scanning technology used in Webroot is revolutionary in many respects. Unlike traditional solutions that perform scans locally on the device, Webroot performs many of its analyses in the cloud. This design minimizes the strain on system resources while maximizing scanning speed and efficiency. With much of the heavy lifting done in the cloud, users won’t experience the lag often associated with large file scans. It also ensures that users benefit from the power of advanced algorithms and vast datasets without burdening their local machines.
"Every security layer brings users one step closer to ensuring their online safety. Webroot's blend of real-time monitoring, automatic updates, behavioral detection, and cloud-based efficiency places it significantly ahead in the game of digital protection."
In summary, these key features make Webroot Anti-Spyware not just a tool, but a dependable ally in the fight against spyware. Each element works harmoniously to offer users a robust defense strategy, making the software a noteworthy consideration for anyone serious about safeguarding their online presence.
Installation and Setup
The process of installation and setup is crucial when it comes to utilizing Webroot Anti-Spyware. A well-managed setup ensures that the software functions as intended, keeping your device safe from spyware threats. Understanding the specific installation parameters can clear the path toward seamless protection and a smoother user experience. This section will dive into the technical requirements and provide a straightforward, step-by-step guide to get you up and running.
System Requirements for Installation
Before you dive into the setup, it's important to make sure your system aligns with Webroot’s requirements. This not only guarantees smooth installation but also optimal performance once the software is running. Here are the key requirements:
- Operating System: Webroot is compatible with Windows, Mac, and certain Linux distributions. Ensure your OS is updated to at least Windows 10 or macOS Mojave.
- RAM: A minimum of 2 GB is recommended for basic functionality, but more is preferable for advanced features.
- Storage Space: At least 250 MB of free disk space is essential for installation.
- Internet Connection: A stable internet connection is crucial. Webroot implements cloud-based scanning, which relies heavily on real-time data exchange.
Once your system meets these specifications, you're ready to go to the next stage. Remember, even if you have the latest hardware, mismatched software configurations can lead to future complications.
Step-by-Step Installation Guide

Now that you've confirmed your system's requirements, let us walk through the installation process for Webroot Anti-Spyware. This guide aims to make things as simple as pie:
- Download the Installation File: Begin by visiting Webroot's official site. Locate the download section, and choose the version that fits your operating system. This is often available on https://www.webroot.com.
- Locate the File: Once the download finishes, navigate to your download folder. Look for the Webroot installer, usually named something like for Windows or for Mac.
- Run the Installer: Double-click on the installation file. Windows users may need to provide permission for the file to run, which can sometimes require approval from a user account control pop-up.
- Follow the Prompts: The installation wizard will guide you through the process. Accept the license agreement and select the appropriate installation preferences. You can typically stick with default settings unless you have specific needs.
- Enter Activation Key: If you’ve purchased a subscription, you’ll need your activation key. It’s often in the purchase confirmation email. Enter it when prompted to unlock full features.
- Complete Installation: Click the finish or install button. The process could take a few minutes.
- Update Definitions: After installation, it's good practice to ensure the software is updated with the latest spyware definitions. Open the Webroot interface and look for any update options to download the latest protection updates.
- Conduct an Initial Scan: To confirm everything is working as it should, perform an initial scan. This step establishes a baseline of your system’s health.
Proper installation is the bedrock of reliable spyware protection. Don’t rush through these steps.
By following these simple instructions, you can set up Webroot Anti-Spyware without a hitch. Ensuring that each stage is approached with care lays the groundwork for effective online security.
User Experience and Interface
When it comes to software like Webroot Anti-Spyware, the user experience and interface are vital in determining how effectively users can protect themselves from online threats. A well-designed interface not only enhances functionality but also makes a security tool more accessible, ensuring that both beginners and seasoned users can navigate it with ease.
Navigating the User Interface
Navigating the user interface of Webroot is generally straightforward. The design leans heavily on intuitiveness, which is a significant boon for those who may not be tech-savvy. Upon launching the program, users are greeted with a clean dashboard that emphasizes key information, such as system status and recent scan results. This minimizes the chances of users feeling lost in a maze of complex settings or features.
Some specific aspects of navigation include:
- Clear Visual Indicators: The dashboard features easy-to-read icons and colored status indicators that provide immediate feedback on the system’s health.
- Logical Layout: Users can quickly access essential functions like scanning and settings through a side menu, reducing the time it takes to find specific tools.
- Help Sections: Integrated tips and help sections guide users through complex functionalities, making learning easier.
A well-designed user interface doesn’t just make life easier; it can actually impact the effectiveness of the software itself. The quicker the user can operate the tool, the more likely they are to adapt safe online practices.
"A handy interface transforms complex tasks into a walk in the park, ultimately empowering users to safeguard their digital lives."
Ease of Use for Beginners and Experts
The ease of use of Webroot is another highlight of its design philosophy. For newcomers to anti-spyware solutions, the learning curve can often be steep. Webroot mitigates this challenge through a user-friendly setup and streamlined functionalities that don’t overwhelm.
Nevertheless, the software doesn’t skimp on features that experienced users might desire.
Some points on usability include:
- Setup Wizard: Upon installation, a simple setup wizard prompts users through the initial configuration. This takes away the guesswork.
- Customizable Settings: For those familiar with anti-spyware, the option to tweak settings provides flexibility without compromising usability.
- One-Click Operations: With options for quick scans and full scans just a click away, users can efficiently manage their security tasks without deep-diving into menus.
Performance and Effectiveness
In the world of online security, the performance and effectiveness of an anti-spyware tool are paramount. With the increasing evolution of spyware threats, users require a solution that not only detects these threats but also operates efficiently in the background without hindering overall system performance. This section explores how Webroot Anti-Spyware excels in these areas, providing relevant insights and considerations for users.
Detection Rates Against Spyware
When evaluating anti-spyware solutions, one cannot overlook the detection rates. High detection rates mean that the software can identify a vast majority of spyware threats, ensuring that users stay protected from malicious intrusions. Webroot boasts impressive detection capabilities, utilizing a unique blend of cloud-based technology and behavioral detection. Unlike traditional methods, which often rely on extensive databases of known threats, Webroot takes a proactive stance by analyzing the behavior of applications in real-time.
This approach means that if an unknown or newly emerged spyware tries to infiltrate the system, Webroot can capture its activity and determine potential risks before it can cause harm. According to various independent tests, Webroot’s detection rates frequently reach upwards of 99%, effectively ranking it among the top players in the anti-spyware market. This level of efficacy can instill considerable confidence in users who are worried about the constant evolution of cyber threats.
"In a digital landscape that's ever-changing, staying a step ahead is non-negotiable. Webroot's detection rates demonstrate a commitment to this principle."
Impact on System Performance
Next on the radar is how anti-spyware solutions interact with the everyday performance of your system. Users, particularly those who perform resource-intensive tasks such as video editing or gaming, often worry that security software will slow down their systems. Webroot, however, is designed with efficiency in mind.
One of the standout features is its cloud-based scanning. This means that the heavy lifting is done on remote servers rather than local machines, significantly reducing the load on a user's hardware. As a result, users experience minimal interruptions or lag while browsing, gaming, or multitasking. It has been noted that many users report a smoother experience when using Webroot compared to other traditional anti-spyware products that can become resource hogs.
Moreover, automatic updates provide an additional layer of efficiency. Because Webroot continuously updates its threat database in real-time, users benefit from having the latest security measures without having to initiate tedious manual updates.
In summary, when it comes to performance and effectiveness, Webroot Anti-Spyware hits a sweet spot. High detection rates backed by efficient cloud technology result in a robust line of defense without compromising system speed. For anyone concerned about spyware threats while wanting to maintain a seamless user experience, Webroot could be a compelling choice.
Comparative Analysis
The realm of anti-spyware solutions is vast and varied; hence, undertaking a comparative analysis is not merely beneficial, it’s essential. By contrasting Webroot against other anti-spyware programs, users gain clarity on where Webroot stands and what unique advantages—or drawbacks—it may present.
Webroot vs. Other Anti-Spyware Solutions
When juxtaposing Webroot with its counterparts like Malwarebytes, Norton AntiVirus, or Bitdefender, a few key aspects come to light. Each of these solutions has developed its own arsenal against spyware, but they also differ widely in performance, usability, and additional features.
One of Webroot’s main selling points is its cloud-based scanning technology, which allows it to identify threats without pulling excessive resources from local systems. In contrast, some competitors may lean heavily on on-device analysis, which can drag down system performance significantly. Users often report quicker scans with Webroot due to its unique architecture, decreasing the likelihood of being held up during everyday tasks.
Additionally, Webroot is frequently praised for its ability to stay lightweight while delivering strong protection. This efficiency often translates to a lower impact on system resources, catering especially well to those using older machines or those who wish to maintain high performance during intense computing tasks.
However, on the flip side, some might argue that Webroot doesn’t have the extensive historical database of threats that established players like Norton boast. This could potentially result in a lag in the detection of newly emerging threats. Yet Webroot makes a case for its efficiency through regular updates that keep its database fresh and relevant.
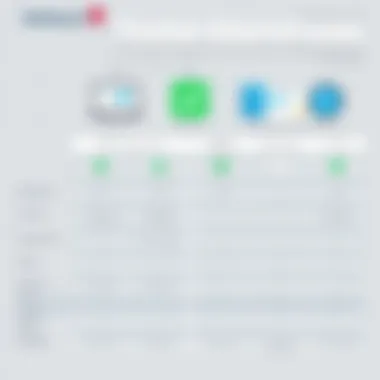

- Pros of Webroot:
- Cons of Webroot:
- Lightweight and fast
- Cloud-based scanning
- Effective real-time protection
- May lack the depth of local threat databases compared to others
Choosing the Right Anti-Spyware for Your Needs
Understanding your unique requirements is paramount when selecting an anti-spyware solution. Consideration should extend beyond mere pricing and advertisements. Instead, ask yourself: what do you need from such a program?
- User Environment: Are you using a personal computer, or are you managing a network of systems? For individual use, lightweight software like Webroot might suffice. However, in a business setting, more comprehensive solutions may offer centralized management features that can be beneficial.
- System Compatibility: Is your device running an older operating system? Ensure the chosen anti-spyware is compatible. Some programs function well on contemporary platforms but falter on earlier versions.
- Performance Implications: How critical is system speed and responsiveness for you? If your primary concern is multitasking, Webroot's efficient use of resources might be more appealing than bulkier alternatives.
Evaluating these factors against the backdrop of comparative analysis can help you find a balance that meets your specific needs while keeping your data secure.
“Selecting the right anti-spyware is like choosing the right tool for the job; it should be tailored to fit your exact needs, not just a popular choice among the crowd.”
Customer Support and Resources
In today’s digital arena, where threats to online privacy and security lurk at every corner, customer support for software like Webroot Anti-Spyware becomes not just an accessory, but an essential lifeline for users. Understanding the types of support available can make a considerable difference in a user’s experience, especially during moments of crisis. The necessity of effective customer support cannot be overstated, as it ensures that users feel secure knowing help is readily available when navigating complex security issues. In this section, we'll explore the various support channels Webroot provides, as well as the community and knowledge resources that enhance user experience.
Available Support Channels
Webroot offers a variety of support channels tailored to help users effectively address their concerns. These channels include:
- Online Help Center: A dedicated portal where users can access comprehensive articles, guides, and FAQs covering numerous topics ranging from installation to troubleshooting.
- Email Support: Users can reach out via email for queries that might require more detailed attention. Typically, responses are swift, ensuring users aren’t left in the lurch for long.
- Phone Support: For immediate assistance, Webroot provides a toll-free number wherein representatives are available to resolve issues directly, lending a personal touch to tech support.
- Live Chat: This option allows users to connect with support staff in real-time, perfect for those who prefer interactive problem-solving without picking up the phone.
These channels are designed to cater to a diverse range of user preferences. With these tools at their disposal, users can quickly connect to assistane and mitigate issues effectively, reducing downtime and enhancing their overall experience with Webroot.
Community and Knowledge Resources
In addition to direct support channels, the value of community-driven resources cannot be overlooked. Here’s why engaging with them can significantly benefit users:
- User Forums: Webroot’s community forums allow users to share experiences and solutions. Interacting with fellow users often leads to discovering tips that official materials might overlook.
- Knowledge Base Articles: A treasure trove of information, these articles cover everything from basic queries to advanced troubleshooting steps, empowering users to resolve many issues independently.
- How-to Videos: Visual learners can take advantage of instructional videos that demonstrate various processes, such as installation or specific troubleshooting techniques.
- Social Media Interaction: Following Webroot on platforms like Facebook or Reddit provides users with timely updates, discussions, and insights into the latest developments in online security, making users feel more connected.
In a world where threats evolve rapidly, being equipped with solid support and resources is crucial.
"The transformation of online security starts with understanding and utilizing the resources available to you."
Thus, whether it’s personal troubleshooting or engaging with a broader community, Webroot’s supportive network is designed to bolster users' confidence in their online safety. It’s not merely about purchasing a product; it’s about investing in peace of mind that comes from knowing you're not navigating the treacherous waters of the internet alone.
Pricing and Licenses
When considering any software, especially one geared towards online security like Webroot Anti-Spyware, Pricing and Licenses play a crucial role. This section delves into how pricing structures work, what options users have, and the implications of these choices on the overall security landscape. Some folks might skip over this part, thinking it’s all about features and functionalities. But, the reality is, understanding the costs involved can impact not just your budget but the effectiveness of the security solutions you choose. This discussion will lay out the different pricing plans and assess the value they offer relative to their services.
Different Pricing Plans Offered
Webroot boasts a variety of pricing plans to cater to users with different needs. Here’s a look at what’s on offer:
- Individual Plans: These are ideal for personal use, starting at a competitive price point that makes it approachable for the everyday user.
- Family Plans: Designed for households, these allow multiple devices to be protected under one umbrella. A typical family plan covers up to five devices and is often priced around $59.99 annually.
- Business Plans: For small to mid-sized businesses, Webroot offers tailored solutions with varying levels of coverage, suited for different business sizes and operations. Pricing often starts at around $249.99 yearly for basic packages.
- For example, a single device plan often costs around $29.99 per year.
"Investing in a robust anti-spyware solution isn’t just penny-pinching; it’s about securing peace of mind in online spaces where threats loom large."
Value in Relation to Services Provided
The value of Webroot’s pricing is evident when you scrutinize the services included within each plan. Sure, you might pay a bit upfront, but what are you really getting for your money?
- Real-Time Protection: This alone justifies most of the cost. It's high-tech monitoring that keeps dangerous threats at bay as they occur, rather than after the fact.
- Automatic Updates: Regular updates ensure your protection is always running on the latest definitions, which can be a lifesaver.
- Behavioral Detection: This feature turns the effectiveness of Webroot into something tangible, catching threats based on suspicious activity rather than known signatures alone.
- Cloud-Based Scanning: Users receive the benefits of high-speed scanning without bogging down their system, which is a great plus for those with older machines.
In summary, while Webroot's prices might not always be the lowest on the market, the comprehensive protection and pioneering technology they offer often makes it a worthwhile investment for those serious about online safety.
The End
In an age where online threats are ever-evolving, the conversation around anti-spyware solutions like Webroot becomes increasingly critical. Understanding the multifaceted nature of Webroot not only illuminates its role in safeguarding digital environments but also underscores the significance of proactive measures against spyware. In these final reflections, it’s essential to crystallize the core themes explored throughout this article.
Summary of Key Points
- Understanding of Anti-Spyware: This article examined the basic functionality of anti-spyware technology, detailing its purpose and how spyware operates. The necessity for reliable anti-spyware tools is founded on the growing sophistication of online threats.
- Webroot’s Features and Performance: From real-time protection to cloud-based scanning, Webroot offers a robust arsenal against spyware. The analysis of its key features demonstrated how they contribute effectively to user security.
- User Experience and Installation: A streamlined installation process and user-friendly interface ensure that both neophytes and seasoned users can navigate the application with ease.
- Pricing Structure: Different plans cater to a range of budgets, ensuring that quality online security can be accessible.
Final Recommendations for Users
As digital privacy becomes a paramount concern, it is advisable to consider your specific needs before settling on an anti-spyware solution. Here are some tailored recommendations:
- Assess Your Online Behavior: Understand your own habits online. If you often visit less-traveled websites or download files from unverified sources, a strong security solution is imperative.
- Utilize Free Trials Wisely: Many providers, including Webroot, offer trial versions. Use this opportunity to test features and performance before committing.
- Stay Updated: The cybersecurity landscape is constantly changing. Regularly check for updates not just for the software but also for emerging threats. This proactive attitude can substantially improve your protection.
- Educate Yourself: Inform yourself about the types of spyware and other malware. Knowledge is power, and being aware of potential threats will help you make smarter choices online.
"In the realm of digital safety, knowledge coupled with the right tools can create an impenetrable fortress against unwelcome intrusions."







